Cybersecurity Services
for Connected Products
Creating more Secure Consumer Devices
With the proliferation of connected devices in the Web 3.0 revolution, Cybersecurity is increasingly becoming crucial to the protection of data, digital personas and business processes from those with criminal intent.
An increasingly indispensable element of the digital world, Cybersecurity ensures the protection of networks, devices and data from unauthorized access – and with the current Web 3.0 revolution accelerating the number of connected devices to never-before-seen levels, it will only continue to become more important to ensure confidentiality, integrity and availability of information.
Bureau Veritas provides a comprehensive range of Cybersecurity Testing, Certification, Training and Assessment services to our clients, helping them build secure devices for consumers, businesses and society. We are helping businesses globally rise to the challenges they face in the digital sphere, to attain new standards and ensure compliance with the latest certifications across the full supply chain.
BUREAU VERITAS EXPANDS CYBERSECURITY OFFER WITH SECURA
Bureau Veritas has completed the acquisition of Secura B.V. (starting with a majority stake), an independent service company specializing in cybersecurity services. Secura will be a cornerstone in the cybersecurity strategy of Bureau Veritas.
Read More
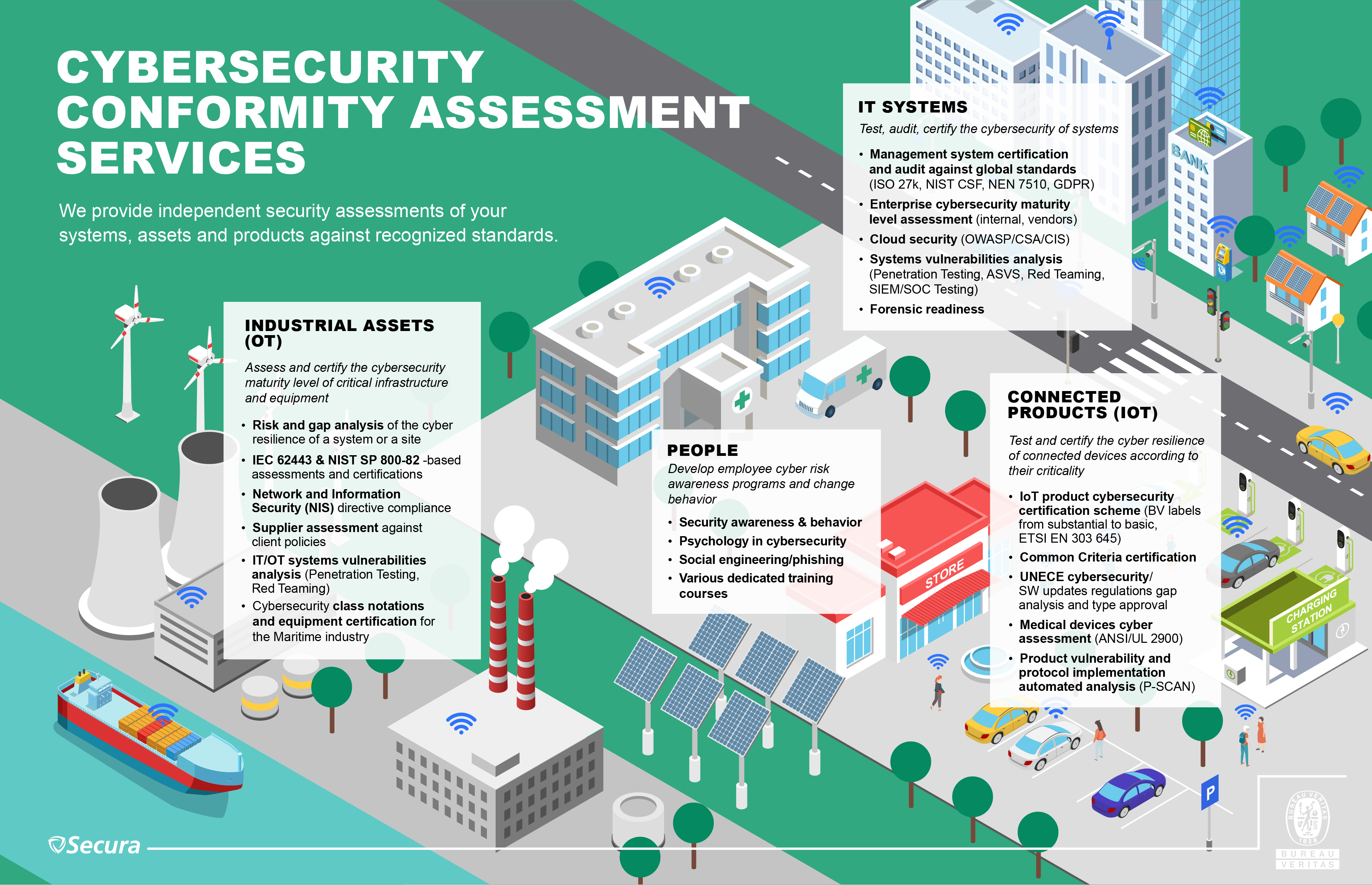
Discover the independent security assessments we provide to our customers in terms of cybersecurity of systems, assets and products against recognized standards.
OUR SERVICES
Bureau Veritas is your partner in the world of product security evaluation, compliance and certification. Our portfolio of possible services includes a broad selection of standards and certification schemes, covering multiple product domains. Because of this, we define our services in line with Development, Support and Preparation, Compliance and Testing and Certification, for various types of connected products. This is summarized below.
|
Support and Preparation |
- Design Reviews |
|
Compliance and Testing |
- ETSI EN 303 645 |
|
Certification |
- OWASP |
|
Support and Preparation |
- Design Reviews |
|
Compliance and Testing |
- IEC 62443 Compliance |
|
Certification |
- IECEE certification (IEC 62443) |
|
Support and Preparation |
- Review of Processes and Consultancy in Drafting/Implementation |
|
Compliance and Testing |
- ISO/SAE 21434 Compliance Gap Analysis |
|
Certification |
- UNECE Cybersecurity (R155) and Software Updates (R156) Compliance Gap Analysis |
|
Support and |
- Design Reviews |
|
Compliance and Testing |
- IEC 62443 Compliance |
|
Certification |
- UL 2900 Certification |
White Paper Download